|
|
|
Stakhov А.P.
International Club of the Golden Section
6 McCreary Trail, Bolton, ON, L7E 2C8, Canada
goldenmuseum@rogers.com · www.goldenmuseum.com/
В статье рассматривается новый класс квадратных матриц, названных «золотыми» матрицами. Они являются обобщением классической «фибоначчиевой» Q-матрицы на непрерывную область. «Золотые» матрицы использованы для создания нового криптографического метода. Метод «золотой» криптографии является очень быстрым и простым для технической реализации и может быть использован для криптографической защиты различных телекоммуникационных систем (включая Интернет), работающих в реальном масштабе времени.
We consider a new class of square matrices called the «golden» matrices. They are a generalization of the classical Fibonacci Q-matrix for continuous domain. The «golden» matrices can be used for creation of a new kind of cryptography called the «golden» cryptography. The method is very fast and simple for technical realization and can be used for the cryptographic protection of different telecommunication systems (including Internet) functioning in real scale of time.
- Introduction
In the last decades the theory of Fibonacci numbers [1-3] was reinforced and invigorated by new scientific results and applications [4-31]. Let us consider only two of them.
Fibonacci Q-matrix
In [2] the following square (2ґ 2)-matrix was introduced:
| (1) |
The following property of the nth power of the Q-matrix was proved in [2]:
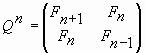 , , |
(2) |
where n = 0, ± 1, ± 2, ± 3, …, Fn-1, Fn, Fn+1 are Fibonacci numbers given by the following recurrence relation:
| Fn+1 = Fn + Fn-1 | (3) |
with the seed:
| F1 = F2 = 1. | (4) |
In the form (2) the Q-matrix shows its connection to the Fibonacci numbers given by (3), (4). It is easy to prove that the determinant of the matrix (2) coincides with the famous «Cassini formula»
| (5) |
that was named in honor of the 17-th century astronomer Giovanni Cassini (1625-1712).
Hyperbolic Fibonacci and Lucas functions
Alexey Stakhov, Ivan Tkachenko and Boris Rozin developed recently a theory of the hyperbolic Fibonacci and Lucas functions [8, 14, 15].
Let us consider so-called symmetrical hyperbolic Fibonacci functions introduced in [15].
Symmetrical hyperbolic Fibonacci sine:
| (6) |
Symmetrical hyperbolic Fibonacci cosine:
| (7) |
where ![]() (the Golden Proportion).
(the Golden Proportion).
Note that the symmetrical hyperbolic Fibonacci functions are connected to the Fibonacci numbers (3), (4) by the following correlations:
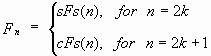 |
(8) |
It was proved in [15] that the following identities connect the symmetrical hyperbolic Fibonacci functions:
| [sFs(x)]2 - cFs(x+1) сFs(x-1) = -1 | (9) |
| [cFs(x)]2 - sFs(x+1) sFs(x-1) = 1. | (10) |
Note that the identities (9), (10) are a generalization of the «Cassini formula» (5) for continuous domain.
The main purpose of the present paper is to develop a theory of the «golden» matrices that are a generalization of the matrix (2) for continuous domain. It is also considered to be a new kind of cryptography, which we call the «golden» cryptography, because it is based on the «golden» matrices.
- The «golden» matrices
Some properties of the Q-matrix
Let us represent the Q-matrix (2) in the following form:
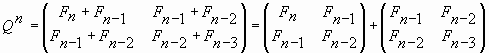 |
(11) |
or
| Qn = Qn-1 + Qn-2. | (12) |
Let us write the expression (11) in the form:
| Qn-2= Qn — Qn-1. | (13) |
It was shown in [2] that the following property of the Q-matrix is valid:
| QnQm = QmQn = Qn+m. | (14) |
A representation of the matrices Qn (n = 0, ± 1, ± 2, ± 3,...) in explicit form based on the recurrence relations (12), (13) are given in Table 1.
Table 1. The explicit forms of the matrices Qn
|
n |
0 |
1 |
2 |
3 |
4 |
5 |
6 |
7 |
|
Qn |
|
|
|
|
|
|
|
|
|
Q-n |
|
|
|
|
|
|
|
|
Note that Table 1 gives the «direct» matrices Qn and their «inverse» matrices Q-n in explicit form. Comparing the «direct» and «inverse» Fibonacci matrices Qn and Q-n given in Table 1 it is easy to see that there is a very simple method to get the «inverse» matrix Q-n from its «direct» matrix Qn. In fact, if the power of the «direct» matrix Qn given with (2) is odd number (n=2k) then for getting of its «inverse» matrix Q-n it is necessary to rearrange in matrix (2) its diagonal elements Fn+1 and Fn-1 and to take its diagonal elements Fn with an opposite sign. It means that for the case n=2k the «inverse» matrix Q-n has the following form:
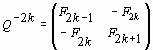 |
(15) |
For the case n=2k+1 for obtaining the «inverse» matrix Q-n from the «direct» matrix Qn it is necessary to rearrange in (2) the diagonal elements Fn+1 and Fn-1 and to take them with an opposite sign, so that one finds:
| (16) |
The direct «golden» matrices
Let us represent now the matrix (2) in the form of two matrices that are given for the odd (n=2k) and even (n=2k+1) values of n:
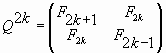 |
(17) |
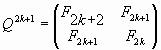 |
(18) |
If we use the correlation (8), we can write the matrices (17), (18) in the terms of the symmetrical hyperbolic Fibonacci functions (6), (7):
| (19) |
| (20) |
where k is a discrete variable, k=0, ± 1, ± 2, ± 3, ….
If we replace now the discrete variable k in the matrices (19), (20) by the continuous variable x, then we will come to the two unusual matrices that are the functions of the continuous variable x:
| (21) |
| (22) |
It is clear that the matrices (21), (22) are a generalization of the Q-matrix (2) for continuous domain. They have a number of the unique mathematical properties. For example, for ![]() the matrix (14) takes the following form:
the matrix (14) takes the following form:
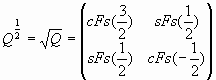 |
(23) |
It is impossible to imagine a meaning for the «square root of the Q-matrix», but such «Fibonacci fantasy» follows from (23) amazing on it may be.
The inverse «golden» matrices
Let us represent the inverse matrices (15), (16) in the terms of the symmetrical hyperbolic Fibonacci functions (6), (7):
| (24) |
| (25) |
where k is a discrete variable, k=0, ± 1, ± 2, ± 3, ….
If we replace now the discrete variable k in the matrices (24), (25) by the continuous variable x, then we will come to the following matrices that are the functions of the continuous variable x:
| (26) |
| (27) |
Let us prove that the matrix (26) is the inverse of the matrix (21). To this end let us calculate a product of the matrices (21) and (26):
| Q2x ґ Q-2x = = 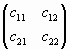 , , |
(28) |
where
| c11 = cFs(2x+1)ґ cFs(2x-1) – [sFs(2x)]2 | (29) |
| c12 = — cFs(2x+1)ґ sFs(2x) + cFs(2x+1)ґ sFs(2x) | (30) |
| c21 = sFs(2x)ґ sFs(2x-1) — sFs(2x-1)ґ sFs(2x) | (31) |
| c22 = — [sFs(2x)]2 + cFs(2x+1)ґ cFs(2x-1) | (32) |
It follows from (30), (31) that
| c12 = c21 = 0 | (33) |
Using the identity (9) we can write the expressions (29), (32) as follows:
| c11 = c22 = 1. | (34) |
Then using (33), (34) we can write the expression (28) in the form:
| Q2xґ Q-2x = |
(35) |
The identity (35), which is valid for any value of the variable x, is a proof that the matrix (26) is the inverse matrix.
In the same manner we can prove:
| Q2x+1ґ Q-2x+1 = |
(36) |
This means that (27) is the inverse matrix to (25).
Determinants of the «golden» matrices
Let us calculate now the determinants of the matrices (21) and (22):
| Det Q2x = cFs(2x+1)ґ cFs(2x-1) – [sFs(2x)]2 | (37) |
| Det Q2x+1 = sFs(2x+2)ґ sFs(2x) – [cFs(2x+1)]2 | (38) |
Let us compare the expression (37) to the identity (8). Because the identity (8) is true for any values of the variable x, in particular, for the value 2x, it follows from this consideration the following identity:
| Det Q2x = 1 | (39) |
By analogy, we can write:
| Det Q2x+1 = - 1 | (40) |
If we now return back to the «Cassini formula» (5), we can conclude that the unusual identities (39), (40) are a generalization of the «Cassini formula» (5) for continuous domain.
- The «golden» cryptography
The «golden» cryptographic method
What we he introduced above, namely the «golden» direct and inverse matrices (21), (22), (26), (27), allow us to develop the following application to cryptography. Let the initial message be a «digital signal», which is any sequence of real numbers:
| a1, a2, a3, a4, a5, a6, a7, a8, … | (41) |
Separate real numbers of the sequence (41) are called readings.
There are many examples of the «digital signals» (41): digital telephony, digital TV, digital measurement systems and so on.
The problem of protecting the «digital signal» (41) from the hackers is solved usually with application of cryptographic methods. Consider a new cryptographic method based on the «golden» matrices.
To this end let us choose the first four readings a1, a2, a3, a4 of (41) and form from them a square 2ґ 2-matrix M:
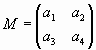 |
(42) |
Note that the initial matrix M can be considered as plaintext [32].
Note that there are 4! = 4ґ 3ґ 2ґ 1 = 24 variants (permutations) to form the matrix (42) from the four readings a1, a2, a3, a4. Let us designate the i-th permutation by Pi (i=1, 2, …, 24). The first step of cryptographic protection of the four readings a1, a2, a3, a4 is a choice of the permutation Pi.
Then we choose the direct «golden» matrices (21) or (22) as enciphering matrices and their inverse matrices (26), (27) as deciphering matrices.
Let us consider now the following encryption/decryption algorithms based on matrix multiplication (see Table 2).
Table 2. Encryption/decryption algorithm
|
Encryption |
Decription |
|
Mґ Q2x = E1(x) |
E1(x)ґ Q-2x = M |
|
Mґ Q2x+1 = E2(x) |
E2(x)ґ Q-2x+1 = M |
Here M is the plaintext (42) that is formed according to the permutation Pi; E1(x), E2(x) are ciphertexts; Q2x, Q2x+1 are the enciphering matrices (21), (21); Q-2x and Q-2x+1 are the deciphering matrices (26), (27). We can use the variable x as a cryptographic key or simply a key. This means that in dependence on the value of the key x there is an infinite number of transformation of the plaintext M into the ciphertext E(x).
In general the key K consists of two parts: permutation Pi and the variable x, that is,
K = {P, x}.
Let us prove that the cryptographic method given with Table 2 ensures one-valued transformation of the plaintext into the ciphertext E and then the ciphertext E into the plaintext M. Let us consider this transformation for the case when we choose the «golden» matrix (21) as the enciphering matrix. For the given value of the cryptographic key x = x1 the «golden» encryption can be represented as follows:
Mґ Q2x = 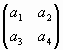 ґ ґ 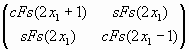 = = 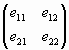 =E(x1) =E(x1) |
(43) |
where
| e11 = a1cFs(2x1+1) + a2sFs(2x1) | (44) |
| e12 = a1sFs(2x1) + a2cFs(2x1-1) | (45) |
| e21 = a3cFs(2x1+1) + a4sFs(2x1) | (46) |
| e22 = a3sFs(2x1) + a4cFs(2x1-1) | (47) |
Let us consider the «golden» decryption for this case:
E(x1)ґ Q-2x = 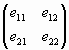 ґ ґ 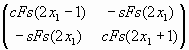 = =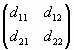 = D = D |
(48) |
where
| d11 = e11cFs(2x1-1) – e12sFs(2x1) | (49) |
| d12 = — e11sFs(2x1) + e12cFs(2x1-1) | (50) |
| d21 = e21cFs(2x1-1) – e22sFs(2x1) | (51) |
| d22 = — e21sFs(2x1) + e22cFs(2x1-1) | (52) |
For calculation of the matrix elements given by (49)-(52) we can use the expressions (44)-(47). Then we have:
| d11 = [a1cFs(2x1+1) + a2sFs(2x1)] cFs(2x1-1) – [a1sFs(2x1) + a2cFs(2x1-1)]sFs(2 x1) =
= a1cFs(2x1+1) cFs(2x1-1) + a2sFs(2x1) cFs(2x1-1) — a1[sFs(2x1)]2 – - a2cFs(2x1-1) sFs(2x1) = a1{cFs(2x1+1) cFs(2x1-1) – [sFs(2x1)]2} |
(53) |
Using the fundamental identity (9) we can write the expression (53) as follows:
| d11 = a1. | (54) |
In the same manner after corresponding transformations we can write:
| d12 = a2 | (55) |
| d21 = a3 | (56) |
| d22 = a4 | (57) |
Using (54)-(55) we can write the matrix D (48) as follows:
D = 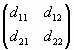 = = 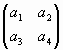 = M = M |
(58) |
This means that a cryptographic method given by Table 2 ensures one-valid transformation of the initial plaintext M at the entrance of the coder into the same plaintext M at the exit of the decoder.
Determinants of the «golden» matrices
Let us calculate now the determinant of the ciphertexts, that is, the matrices E1(x), E2(x):
| Det E1(x) = Det Mґ Det Q2x | (59) |
| Det E2(x) = Det Mґ Det Q2x+1 | (60) |
If we use the identities (39), (40), we can write the expressions (59), (60) in the following form:
| Det E1(x) = Det M | (61) |
| Det E2(x) = — Det M | (62) |
This means that the determinants of the matrices E1(x) and E2(x) is determined identically by the determinant of the initial matrix M.
Encryption and decryption time
According to (43) the encryption consists in calculation of four elements e11, e11, e11, e11 of the matrix (43). According to (44)-(47) a calculation of every element include two multiplications and one addition. This means that a full encryption time Te is equal:
| Te = 8D tm + 4D tad | (63) |
where D tm is a time of one multiplication and D tad is a time of one addition.
By analogy, if we consider the expressions (48)-(52) we can write the expression for a full decryption time:
| Td = 8D tm + 4D tad | (64) |
Analysis of the expressions (63), (64) show that the «golden» cryptography is fast cryptography. This means that the «golden» cryptography can be used for cryptographic protection of digital signals in real scale of time.
Improvement of cryptographic protection
We can improve the cryptographic protection of the method if we use multiple encryption and decryption. This idea consists in the following. The first step of encryption is a use of the key
K1={Pi, x1}
that consists of any permutation Pi and any value x1, taken in random manner. As a result of the encryption we got the matrix E(Pi, x1) given by (43). The second step of encryption is to use the matrix E(x1) as the initial matrix for encryption. To this end we can use the second cryptographic key
K2={Pj, x2}
where Pj is the next permutation and x2 is the next value of x. After performing the «golden» encryption with the key x2 we can get a new matrix E that is a function of the two permutation Pi and Pj and two cryptographic keys x1 and x2, that is, E = E (Pj, x1; Pj, x2). In general case we can repeat this procedure n times, that is, the cryptographic key K is a totality of n random permutations Pi, Pj, …, Pk and n cryptographic keys x1, x2,..., xn, that is,
| K={Pi, x1; Pj, x2;...; Pk, xn } | (65) |
As a result of multiple encryption we can get the matrix
E = E (K).
For the decryption we have to apply the inverse cryptographic key K-1 that is an inverse form of the initial cryptographic key, that is,
K-1 ={ Pk, xn; Pr, xn-1; …; Pj, x2; Pi, x1}.
Transmission of the key
It is clear the «golden» cryptographic method relates to symmetrical cryptography [32]. It is considered now that the main deficiency of the symmetrical cryptography is a problem of key transmission. To this end in the recent decades so-called asymmetrical cryptography was developed [32]. In the asymmetric cryptosystems we use two keys: open or public key and secret key. The encryption of the message before transmission is realized by the public key and the decryption of ciphertext is realized by the secret key. However, the asymmetric cryptography has two deficiencies:
- They use very complicated encryption and decryption algorithms. This means that sometimes they cannot be used for protection of digital signals in real scale of time.
- Because encryption and decryption algorithms are very complicated this fact puts forward a problem to guarantee that encryption and decryption would be realized without errors (a problem of reliable computations).
The «golden» cryptographic method allows us to solve these two problems very elegantly for the following conditions:
- We can use the existing asymmetrical cryptosystems for the transmission of the cryptographic key (65).
- We can use the «golden» cryptographic system given by Table 2 for the fast transmission of the digital signal (41).
- We can use the unique mathematical property of the «golden» cryptography given with (61), (62) for checking of the encryption and decryption algorithms.
This means that using the «golden» cryptography method (Table 2) we can design fast, simple for technical realization and reliable cryptosystems.
Note that for every session of transmission we can change the cryptographic key (65). This means that the analysis of the previous transmissions cannot be used for uncovering of the current cryptographic key (65). We can change the cryptographic key (65) using a generator of random numbers and so on.
- Conclusion
As is shown in [4-31] the application field of the Fibonacci numbers theory applications is developing with such intensity that we can call that it is the beginning of an era of «global Fibonaccization» of modern science. «Harmony Mathematics» [10, 12, 13, 16, 20], which is modern development of the Fibonacci numbers theory, touches the fundamentals of mathematics and can lead to a new number theory [8, 16] and a new measurement theory [4, 5, 7]. The hyperbolic Fibonacci and Lucas functions [8, 14, 15] can lead to creation of Lobachevsky-Fibonacci and Minkovsky-Fibonacci geometry [15] that is of great importance for theoretical physics. However, the works of Mauldin and Willams, El Naschie, Vladimirov [22-31] and other physicists show that it is impossible to imagine a development of modern physical research without deep knowledge of the Golden Section.
The main result of the present article is a development of one more application of the Golden Proportion, that is, a creation of a new kind of matrices called the «golden» matrices. They are an original synthesis of two important discoveries of modern Fibonacci numbers theory, the Fibonacci Q-matrix (2) and hyperbolic Fibonacci functions (6), (7). A new kind of cryptography, the «golden» cryptography, follows from this approach. A common use of the existing asymmetric cryptosystems (for the transmission of the secret key) and the «golden» cryptosystems (for transmission of ciphertexts) can lead to the fast, simple for technical realization and reliable cryptosystems for protection of digital signals used in telecommunication and measurement systems.
References
- [1] Vorobyov NN. Fibonacci Numbers. Moscow: Nauka, 1978 (in Russian)
- [2] Hoggat V.E. Fibonacci and Lucas Numbers. Palo Alto, CA: Houghton-Mifflin; 1969.
- [3] Vajda S. Fibonacci & Lucas Numbers, and the Golden Section. Theory and Applications. Ellis Horwood limited, 1989.
- [4] Stakhov, A.P. Introduction into Algorithmic Measurement Theory, Moscow: Soviet Radio, 1977 (in Russian).
- [5] Stakhov, A.P. Algorithmic Measurement Theory, Moscow: Znanie, Series «Mathematics & Cybernetics», 1979, No 6 (in Russian).
- [6] Stakhov A.P. Codes of the Golden Proportion, Moscow: Radio and Communications, 1984 (in Russian).
- [7] Stakhov, A.P. The Golden Section in the Measurement Theory, Computers & Mathematics with Applications, 1989, Vol. 17, No 4-6, 613-638.
- [8] Stakhov A.P., Tkachenko I.S. Hyperbolic Fibonacci Trigonometry. Reports of the Ukrainian Academy of Sciences, Vol. 208, No 7, 1993, 9-14 (in Russian).
- [9] Stakhov A.P. A generalization of the Fibonacci Q-matrix. Reports of the National Academy of sciences of Ukraine, No 9, 1999, 46-49.
- [10] Stakhov, A.P. The Golden Section and Modern Harmony Mathematics, Applications of Fibonacci Numbers, Kluwer Academic Publishers, 1998, Vol. 7, 393-399.
- [11] Stakhov A.P. Brousentsov’s Ternary Principle, Bergman’s Number System and Ternary Mirror-symmetrical Arithmetic, The Computer Journal (British Computer Society), Vol. 45, No. 2, 2002, 221-236.
- [12] Stakhov A.P. The Generalized Golden Sections and a New Approach to the Geometric Definition of a Number. Ukrainian Mathematical Journal, 2004, Vol. 56, No. 8, 1143-1150 (in Russian).
- [13] Stakhov, A.P. Sacred Geometry and Harmony Mathematics, Vinnitsa: ITI, 2003 (in Russian)
- [14] Stakhov A.P. Hyperbolic Fibonacci and Lucas Functions: A New Mathematics for the Living Nature. Vinnitsa: ITI, 2003.
- [15] Stakhov A., Rozin B. On a new class of hyperbolic function. Chaos, Solitons & Fractals, 2004, 23, 379-389.
- [16] Stakhov A. The Generalized Principle of the Golden Section and its Applications in Mathematics, Science and Engineering. Chaos, Solitons & Fractals, 2005, 26, 263-289.
- [17] Stakhov A., Rozin B. The Golden Shofar. Chaos, Solitons & Fractals, 2005, 26, 677-684
- [18] Stakhov A., Rozin B. Theory of Binet formulas for Fibonacci and Lucas p-numbers. Chaos, Solitons & Fractals, 2006, 27, 1162-1177.
- [19] Stakhov A., Rozin B. The «Golden» Algebraic Equations. Chaos, Solitons & Fractals, 2005, 2006, 27, 1415-1421.
- [20] Stakhov AP Fundamentals of a new kind of mathematics based on the Golden Section, Chaos, Solitons & Fractals, 2005, 27, 1124-1146.
- [21] Spinadel V.W. From the Golden Mean to Chaos. Editorial Nueva Librerнa, Buenos Aires, Argentina, ISBN 950-43-9329-1, 1998, second edition Nobuko, 2004.
- [22] Mauldin R.D. and Willams S.C. Random recursive construction. Trans. Am. Math. Soc. 1986; 295:325-346.
- [23] El Nashie MS. Quantum mechanics and the possibility of a Cantorian space-time. Chaos, Solitons & Fractals 1992, 1: 485-487
- [24] El Naschie MS On dimensions of Cantor set related systems. Chaos, Solitons & Fractals 1993, 3: 675-685
- [25] El Nashie MS. Is Quantum Space a Random Cantor Set with a Golden Mean Dimension at the Core? Chaos, Solitons & Fractals 1994, 4(2): 177-179
- [26] El Naschie MS Statistical Geometry of a Cantor Discretum and Semiconductors. Computer Math. Applic., 1995, Vol.29, No. 12: 103-110.
- [27] El Naschie M.S. Fredholm Operators and the Wave-Particle Duality in Cantorian Space. Chaos, Solitons & Fractals, 1998; 9(6): 975-978.
- [28] El Naschie M.S. On a class of general theories for high energy particle physics. Chaos, Solitons & Fractals 2002; 14: 649-668.
- [29] El Naschie MS. Elementary number theory in superstrings, loop quantum mechanics, twistors and E-infinity high energy physics. Chaos, Solitons & Fractals 2006, 27(2): 297-330.
- [30] Vladimirov Y.S. Quark Icosahedron, charged and Vainberg’s angle. Proceedings of the International Conference «Problems of Harmony, Symmetry and the Golden Section in Nature, Science and Art». Vinnitsa 2003; 15: 69-79 (in Russian).
- [31] Vladimirov Y.S. Metaphysics. Moscow: BINOM, 2002 (in Russian)
- [32] Seberry J, Pieprzyk J. Cryptography: An Introduction to Computer Security. Prentice Hall, 1989.
Stakhov А.P., The «golden» cryptography // «Академия Тринитаризма», М.,
|
|